Here is article I wrote on Terror message detection using AI algorithms.
DOI: 10.13140/RG.2.2.10272.35844
Link: (PDF) Terror Threats Detection using Fuzzy Logic: An Example of Framework (researchgate.net)
Abstract- As terrorism grows so does the incidence of attacks by terror groups. How to detect terror messages on time is a critical issue and scientists need to address this issue with their full commitments. Artificial Intelligence (AI) models can be built to detect terror threats. There are many areas and algorithms in AI that can be used to detect threats. However, many AI algorithms require training data to learn and predict. This is not possible immediately as data collection and training require some time. In this article, we see how an Expert system using the Mamdani Fuzzy Inference Engine can be used in this aspect. Experts in the field of terror analysis shall be required to materialize the so-called Expert System. For now, we are providing a demo skeleton that can be used to understand how the Expert system-based Terror detection works.
1. Introduction
With the increase in terror threats around the world, there are required ways to first detect the terror threat, then to handle it, and to locate the terror suspects before they can attack a place with terror implications. The terror activity can be intercity or out of a city. In this article, we shall propose a generic model, for both in-city/town and out-of-city/town threats. Experts with specialization in terror related fields are requested to edit the details of this article from their perspectives.
Even a small hint of terror messages should be identified. There is a lot of uncertainty associated with terror threats such as the exact place, magnitude, scale, reason, suspect, and target, to mention some. Hence, the best choice we have now is to use Fuzzy Sets which deal with uncertainty with precision and accuracy. Due to the lack of availability of data in the current scenario, we used expert advice-based uncertainty handling with Fuzzy Logic.
Mamdani Fuzzy Logic-based Expert Systems takes the inputs as membership functions of linguistic variables and produces an output that is defuzzied to produce the crisp results. This output can be interpreted by the end-user with the help of the model maker.
The proposed model is given in Section 2, Section 3 provides some illustrations, and Section 4 concludes the article with a glimpse on future work.
2. Proposed Model
The proposed model works on communication networks and servers receiving communication messages from one end to another and vice versa. One should not go into privacy issues here, as this is a demo model. When such an algorithm is set, and used, the users can be assured that their data is just guarded by these algorithms and are not read for any other purpose. The only thing that is required is permission of end-users at the cost of defeating terrorism. Further, the end-users can be guaranteed that the data is not leaked out of the so-called Fuzzy Inference Engine and is safe.
We consider the following Fuzzy Inputs:
- Similarity With Text.
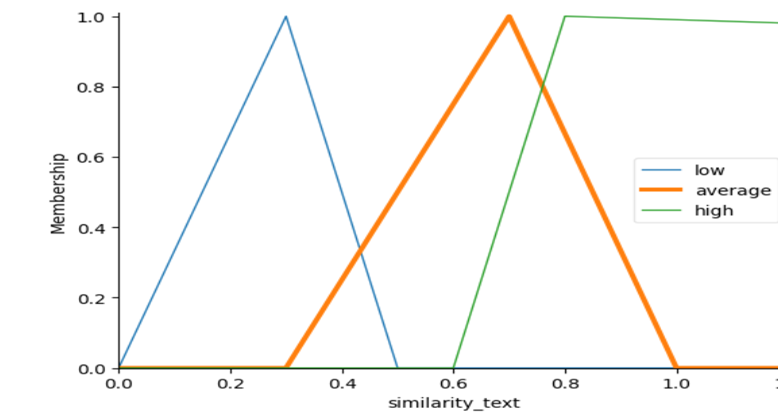
Full article on researchgate as a pre-print.
(PDF) Terror Threats Detection using Fuzzy Logic: An Example of Framework (researchgate.net)
…Please see the above link.
5. Future Work
The models are projected well for explanation and can be taken as a framework for setting the actual Fuzzy Logic based Expert System. However, an expert in this area has to identify the framework in the eyes of real threats. This can be done by contemplating the data that the terror departments have foreseen for ages now.
Further, the experts in the terrorism detection department need to sit with both computer engineers and AI specialists to frame the rules and linguistic input and output variables. The potential for Fuzzy Logic is huge as given we do not have huge data to train deep learning models on this problem, however experts can use other frameworks which use comparatively lessor amount of data.
There is a lot of future work that needs to be done here, given all Fuzzy Linguist variables need to be initialized with precision and rules need to be framed with deliberate emphasis. Once it is ready the Expert System can be used in real-life implementations.